1/7
Rari Capital lost a lot of funds as a result of a complex exploit, right?
However, things are far from simple, and we witnessed the first cross-chain exploit, so let’s see how it went https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">
Rari Capital lost a lot of funds as a result of a complex exploit, right?
However, things are far from simple, and we witnessed the first cross-chain exploit, so let’s see how it went
2/7
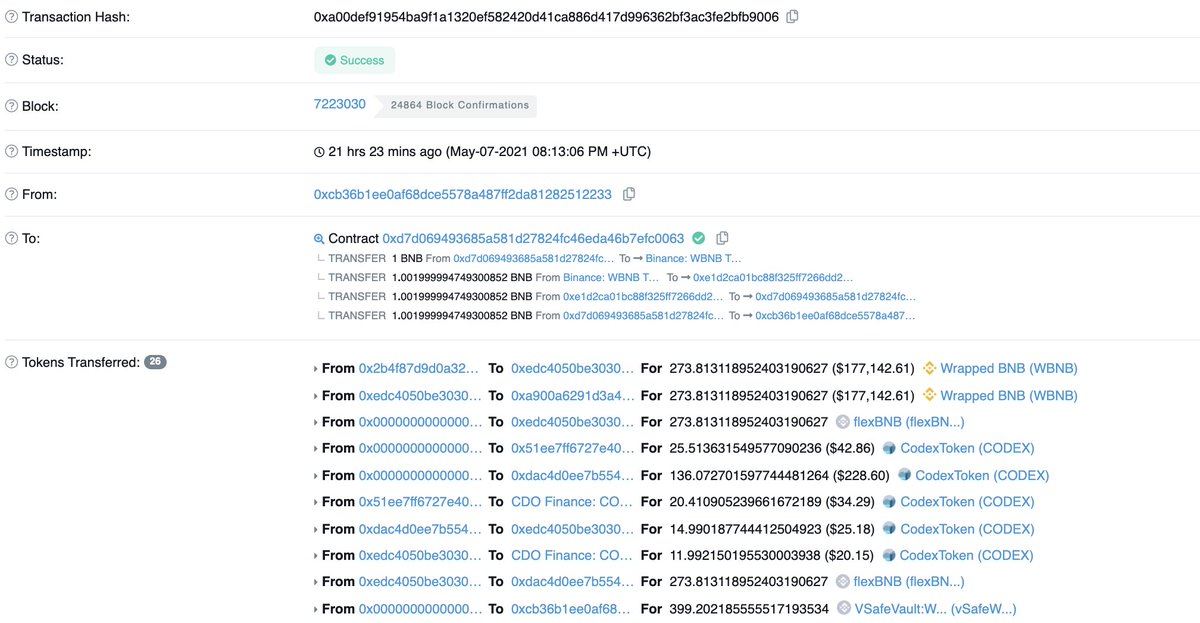
Hackers obtained funds to attack Rari by stealing them from vSafe from @value_defi on BSC (4th attack).
Unfortunately, I was concentrating on the AMM exploit, so I didn’t notice that their yield farm was also affected.
5,346 BNB ($3.8M) were stolen and swapped to 1k ETH.
Hackers obtained funds to attack Rari by stealing them from vSafe from @value_defi on BSC (4th attack).
Unfortunately, I was concentrating on the AMM exploit, so I didn’t notice that their yield farm was also affected.
5,346 BNB ($3.8M) were stolen and swapped to 1k ETH.
3/7
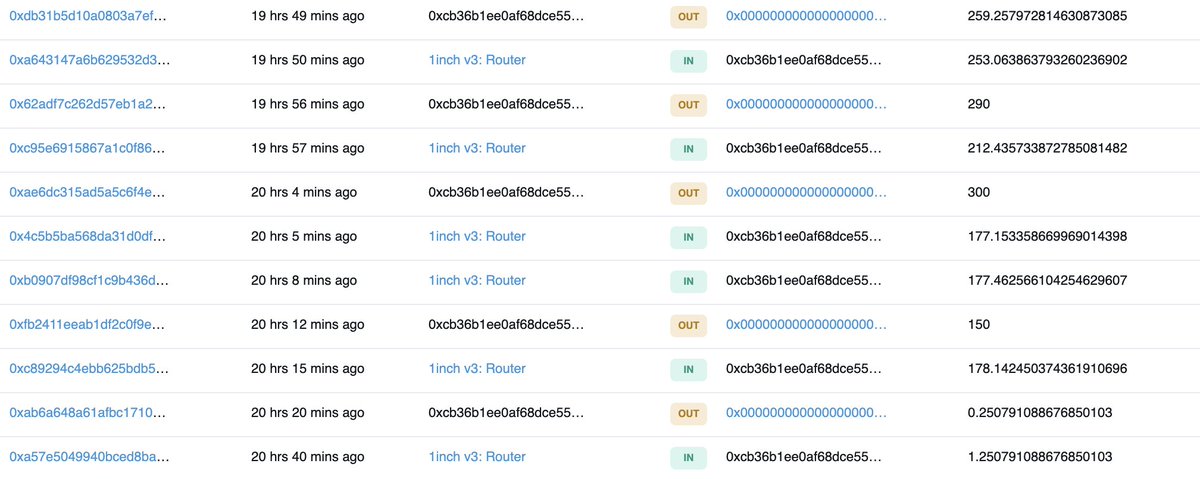
The attacker’s actions on BSC looked like this:
1) Create a fake token and pool on PancakeSwap with it so that Alpaca Finance can be used
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="❗️" title="Rotes Ausrufezeichen" aria-label="Emoji: Rotes Ausrufezeichen"> The next two steps are repeated
https://abs.twimg.com/emoji/v2/... draggable="false" alt="❗️" title="Rotes Ausrufezeichen" aria-label="Emoji: Rotes Ausrufezeichen"> The next two steps are repeated https://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">
The attacker’s actions on BSC looked like this:
1) Create a fake token and pool on PancakeSwap with it so that Alpaca Finance can be used
4/7
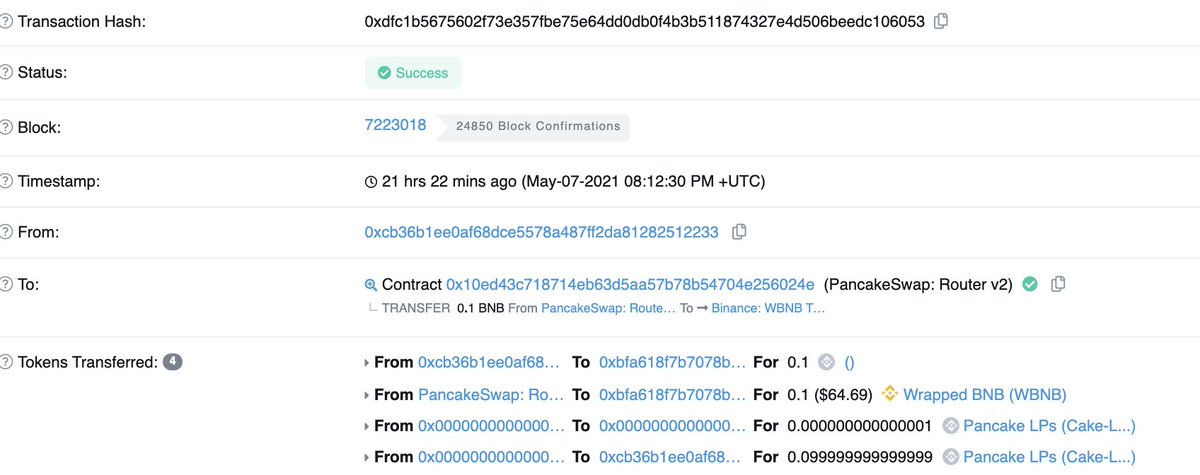
2) Interact with Alpaca Finance, where when calling approve() for a fake token, a payload is called, which allows an attacker to use VSafe through Codex farm to get vSafeWBNB
3) Convert vSafeWBNB to WBNB
4) All WBNB transferred to Ethereum through Anyswap.
2) Interact with Alpaca Finance, where when calling approve() for a fake token, a payload is called, which allows an attacker to use VSafe through Codex farm to get vSafeWBNB
3) Convert vSafeWBNB to WBNB
4) All WBNB transferred to Ethereum through Anyswap.
5/7
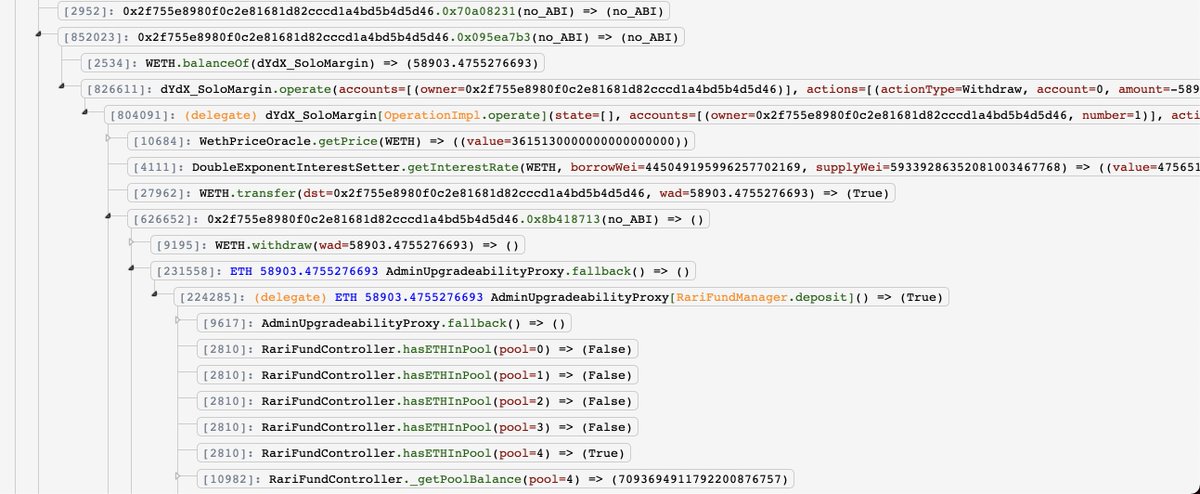
In general, the attack on Rari looked like this:
1) Creating a fake token and pool with it on SushiSwap
 https://abs.twimg.com/emoji/v2/... draggable="false" alt="❗️" title="Rotes Ausrufezeichen" aria-label="Emoji: Rotes Ausrufezeichen"> The next two steps are repeated
https://abs.twimg.com/emoji/v2/... draggable="false" alt="❗️" title="Rotes Ausrufezeichen" aria-label="Emoji: Rotes Ausrufezeichen"> The next two steps are repeated https://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">
https://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">
2) Interaction with Alpha Homora, where a payload is also called so that attacker can get ibETH in the Rari ETH pool contract
In general, the attack on Rari looked like this:
1) Creating a fake token and pool with it on SushiSwap
2) Interaction with Alpha Homora, where a payload is also called so that attacker can get ibETH in the Rari ETH pool contract
6/7
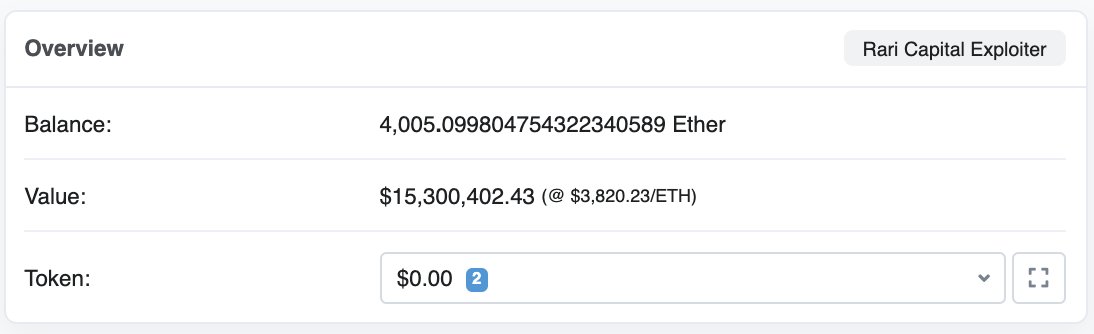
3) Converting ibETH to ETH in Rari ETH pool
As a result, 2.9k ETH ($11.1M) was stolen, and another 1.7k ETH was at risk before the actions of the Rari team.
The total profit from the two attacks was $15M in ETH.
3) Converting ibETH to ETH in Rari ETH pool
As a result, 2.9k ETH ($11.1M) was stolen, and another 1.7k ETH was at risk before the actions of the Rari team.
The total profit from the two attacks was $15M in ETH.
7/7
The interoperability between DeFi protocols is becoming more complex, which opens up new vectors of attacks.
This attack was similar in difficulty to the Pickle Evil Jar and will become even more frequent in the future.
The interoperability between DeFi protocols is becoming more complex, which opens up new vectors of attacks.
This attack was similar in difficulty to the Pickle Evil Jar and will become even more frequent in the future.

 Read on Twitter
Read on Twitter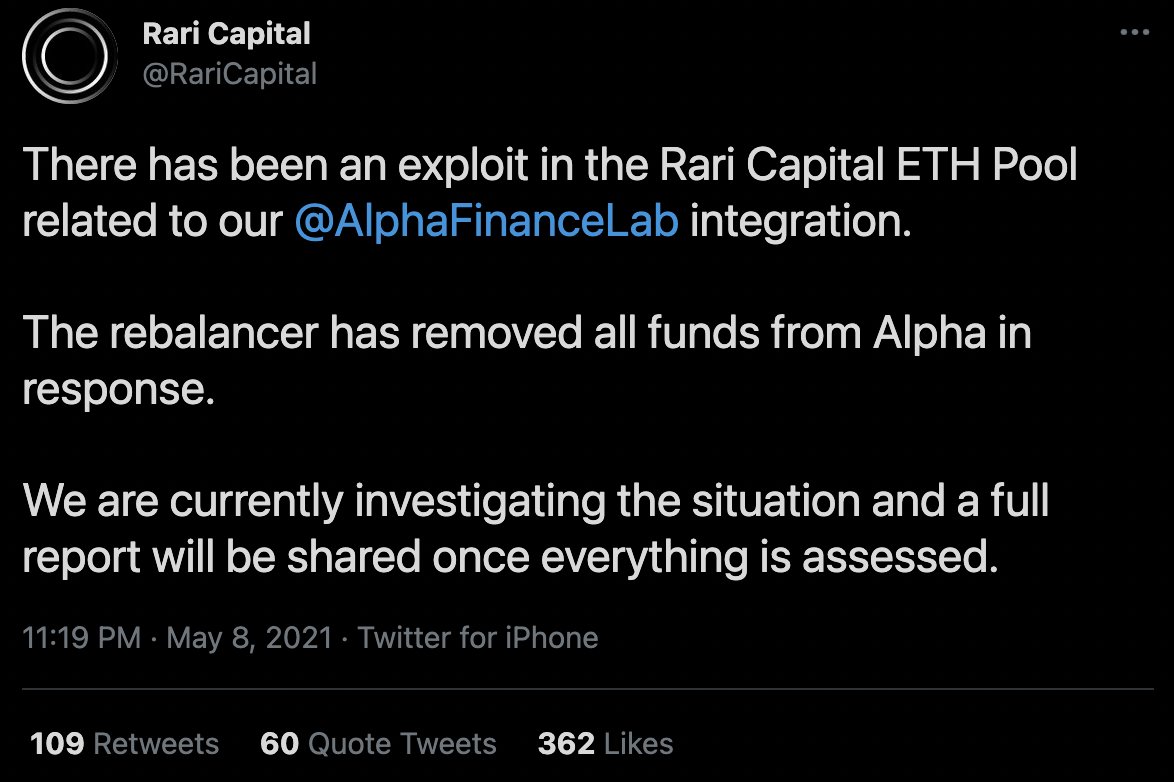 " title="1/7Rari Capital lost a lot of funds as a result of a complex exploit, right?However, things are far from simple, and we witnessed the first cross-chain exploit, so let’s see how it wenthttps://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">" class="img-responsive" style="max-width:100%;"/>
" title="1/7Rari Capital lost a lot of funds as a result of a complex exploit, right?However, things are far from simple, and we witnessed the first cross-chain exploit, so let’s see how it wenthttps://abs.twimg.com/emoji/v2/... draggable="false" alt="👇" title="Rückhand Zeigefinger nach unten" aria-label="Emoji: Rückhand Zeigefinger nach unten">" class="img-responsive" style="max-width:100%;"/>
 The next two steps are repeatedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">" title="3/7The attacker’s actions on BSC looked like this:1) Create a fake token and pool on PancakeSwap with it so that Alpaca Finance can be usedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="❗️" title="Rotes Ausrufezeichen" aria-label="Emoji: Rotes Ausrufezeichen"> The next two steps are repeatedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">" class="img-responsive" style="max-width:100%;"/>
The next two steps are repeatedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">" title="3/7The attacker’s actions on BSC looked like this:1) Create a fake token and pool on PancakeSwap with it so that Alpaca Finance can be usedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="❗️" title="Rotes Ausrufezeichen" aria-label="Emoji: Rotes Ausrufezeichen"> The next two steps are repeatedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">" class="img-responsive" style="max-width:100%;"/>
 The next two steps are repeatedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">2) Interaction with Alpha Homora, where a payload is also called so that attacker can get ibETH in the Rari ETH pool contract" title="5/7In general, the attack on Rari looked like this:1) Creating a fake token and pool with it on SushiSwaphttps://abs.twimg.com/emoji/v2/... draggable="false" alt="❗️" title="Rotes Ausrufezeichen" aria-label="Emoji: Rotes Ausrufezeichen"> The next two steps are repeatedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">2) Interaction with Alpha Homora, where a payload is also called so that attacker can get ibETH in the Rari ETH pool contract" class="img-responsive" style="max-width:100%;"/>
The next two steps are repeatedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">2) Interaction with Alpha Homora, where a payload is also called so that attacker can get ibETH in the Rari ETH pool contract" title="5/7In general, the attack on Rari looked like this:1) Creating a fake token and pool with it on SushiSwaphttps://abs.twimg.com/emoji/v2/... draggable="false" alt="❗️" title="Rotes Ausrufezeichen" aria-label="Emoji: Rotes Ausrufezeichen"> The next two steps are repeatedhttps://abs.twimg.com/emoji/v2/... draggable="false" alt="🔄" title="Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn" aria-label="Emoji: Pfeile abwärts und aufwärts in offenem Kreis gegen den Uhrzeigersinn">2) Interaction with Alpha Homora, where a payload is also called so that attacker can get ibETH in the Rari ETH pool contract" class="img-responsive" style="max-width:100%;"/>